Every devices are learnt by user.
POSIX/LINUX system
Virtual private server separates a member of server from the other, so when one is screwing up, it wouldn't affect the rest of the members.
Example: Github Pages
Open System Interconnected Models
Please Do Not Throw Sausage Pizza Away (lower to higher)
- Physical: wires, fiber optic, copper, radio
- Datalink: Ethernet, MAC Address (Ethernet address for Wifi) <en0 being the one used to talk to Wifi> look up by ifconfig
- Network: public/private IP addresses (e.g, computer IP address, website IP address)
- Transport: TCP (a bunch of bytes being sent to a header), UTP (send and forget, e.g, audio & visual bcs if you lose just a byte it wouldn't really affect much)
- Session
- Presentation: HTML
- Application
-> traceroute : see how your computer hops network until it gets into the address destination depending on Internet traffic
-> CDN: content delivering network
CLI
ps check out all the process that's happening (you can kill them too)
cat /dev/cu/modem101 >> index.html
> overwrites
>> append content
nc 10.20.54.224 80 go to an IP address via netcat
nc -uklw 2 8080
nc -nklw 2 80 2 is the timeout (this command is made but the person who sets up the 10.20.54.224 address)
-nklw is flag
MQTT (Queueing): good for sensors, based on TCP-k → keep listening
- Don’t exit after one connection
- Accept multiple connections, one after another
-l → listen mode
- Act as a server
- Wait for incoming connections
-w 10 → timeout = 10 seconds
- This is the idle timeout
- If no data is sent or received for 10 seconds,
nccloses the connection - The TCP connection will queue the incoming Arduino data
nslookup www.example.com
Geography of the Internet
Network distance: how many nodes you hop before arriving at your destination node?
The greater the density of links in a network, the more possible paths there are for the message to get through to the end point, and the less critical any node is to the functioning of the network -> So is "Distributed/Decentralized Network" more favorable?
TCP -> reliability and order, connection-oriented (handshake) before sending data & ensuring all packets arrive correctly and in order. Ideal for web browsing & email.
UDP -> speed and efficiency. Connectionless, sending data packets without connection or delivery guarantee. Ideal for real-time apps (streaming, gaming). Losing a few pixel / bytes is okay.
Media Access Control (MAC) -> hardware address, 6 bytes, the first 3 bytes is Organizational Universal Identifier, last 3 bytes is your unique ID
For a network made up of n nodes, to be complete, it must have (n2-n)/2 links.
To count the number of links, [add all of the links connected to each node] / 2.
Clustering in network, strong ties between node neighbor vs weak ties across network
Arduino 303 IoT Scan Networks
My pobrecita laptop broke and I'm doing this over the OP ITP computer.. Installed WifiNina and Arduino SAMD and managed to scan a number of networks on the Serial Monitor:
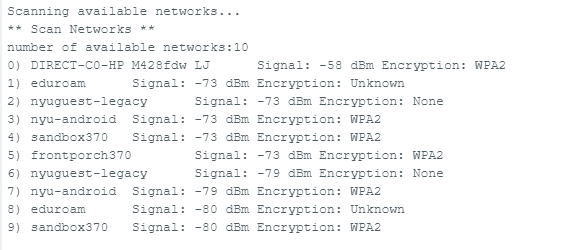
Curious question.. if the Encryption is Unknown, does that mean the network completely unprotected (other than the fact that it is probably a public free Wifi)? How would one attack it? (relating to the Applied Cryptography class that I'm trying to register but got credit maxed out) -> looking for weak/reused password (attacker use the known plaintext attack?), observing handshakes that occur in the victim's network (Known Plaintext Attack!), stealing credentials (by luring user to faux access point) instead of direct attack on encryption algo/finding the key.nc -l 8080 | tee log.json &
tee is the command to split the piping to: (1) terminal & (2) file name
There's some issue between making sure that either the terminal, the port in the localhost website, or the Arduino serial monitor should be open or not. Sometimes one being opened first or concurrently is causing the failure of receiving the sensor message.
Issues
1. Using phone hotspot
Mobile hotspot doesn’t assign computer an IP in the same subnet as Arduino.
Exercise
Receiving input from A0 and A1 that maps to sensorX & sensorY, which controls the mouse position on the JS sketch.
Elizabeth Kezia Widjaja © 2026 🙂